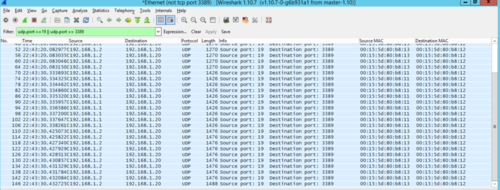
When the Sky is Falling Network-Scale Mitigation of High-Volume Reflection/ Amplification DDoS Attacks. - ppt download

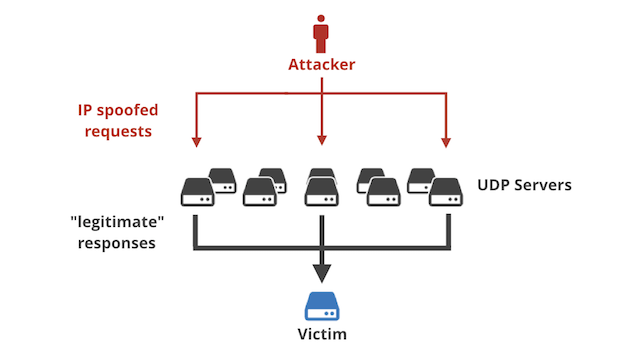
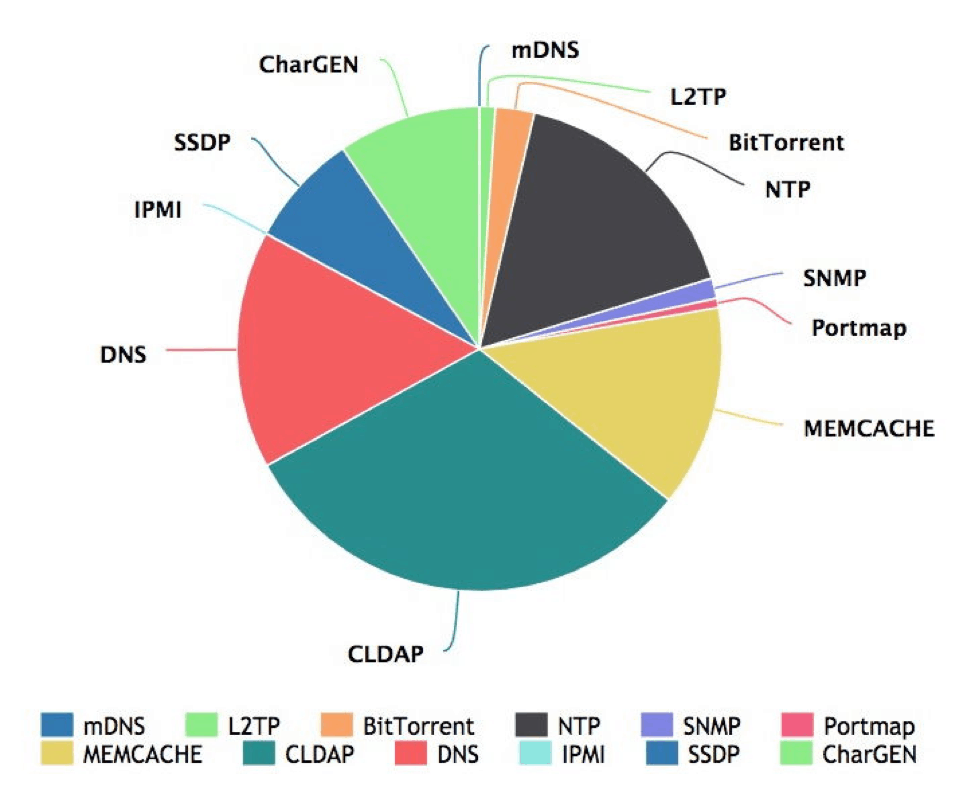
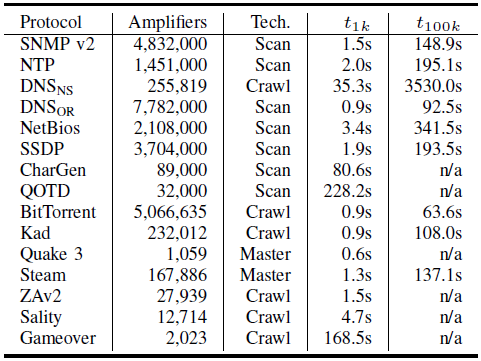
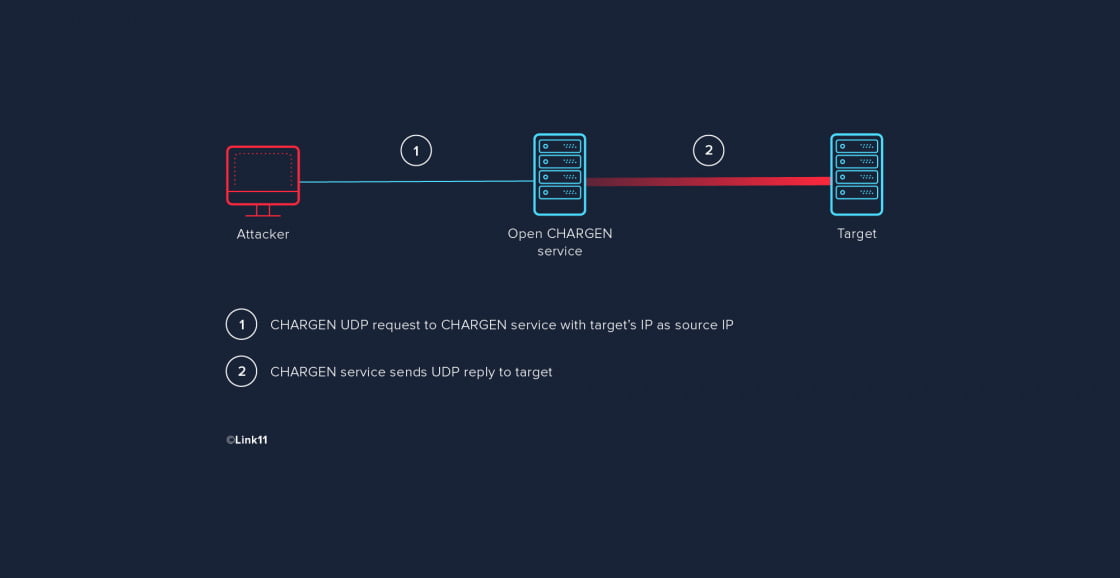
DDOS. Methods – Syn flood – Icmp flood – udp Common amplification vectors – NTP 557 – CharGen 359 – DNS 179 – QOTD 140 – Quake 64 – SSDP 31 – Portmap28. - ppt download

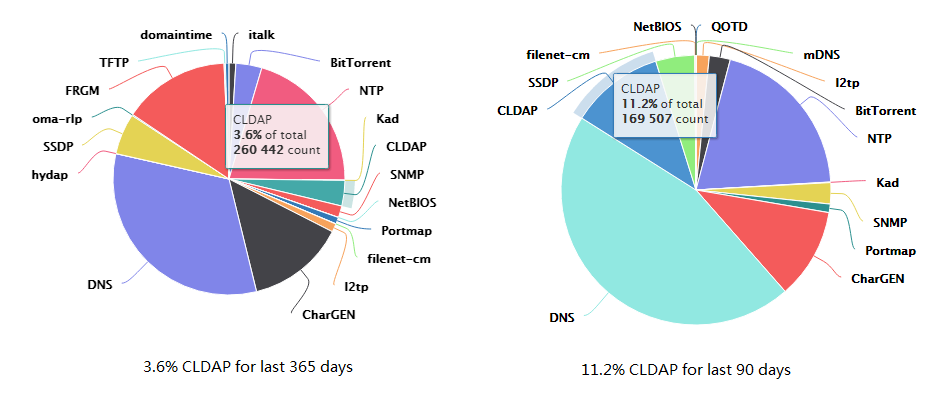
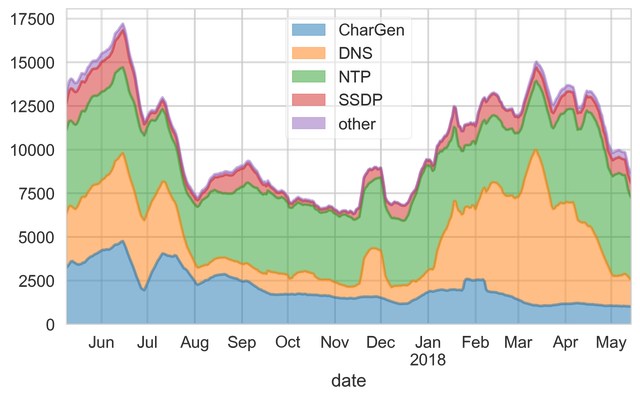
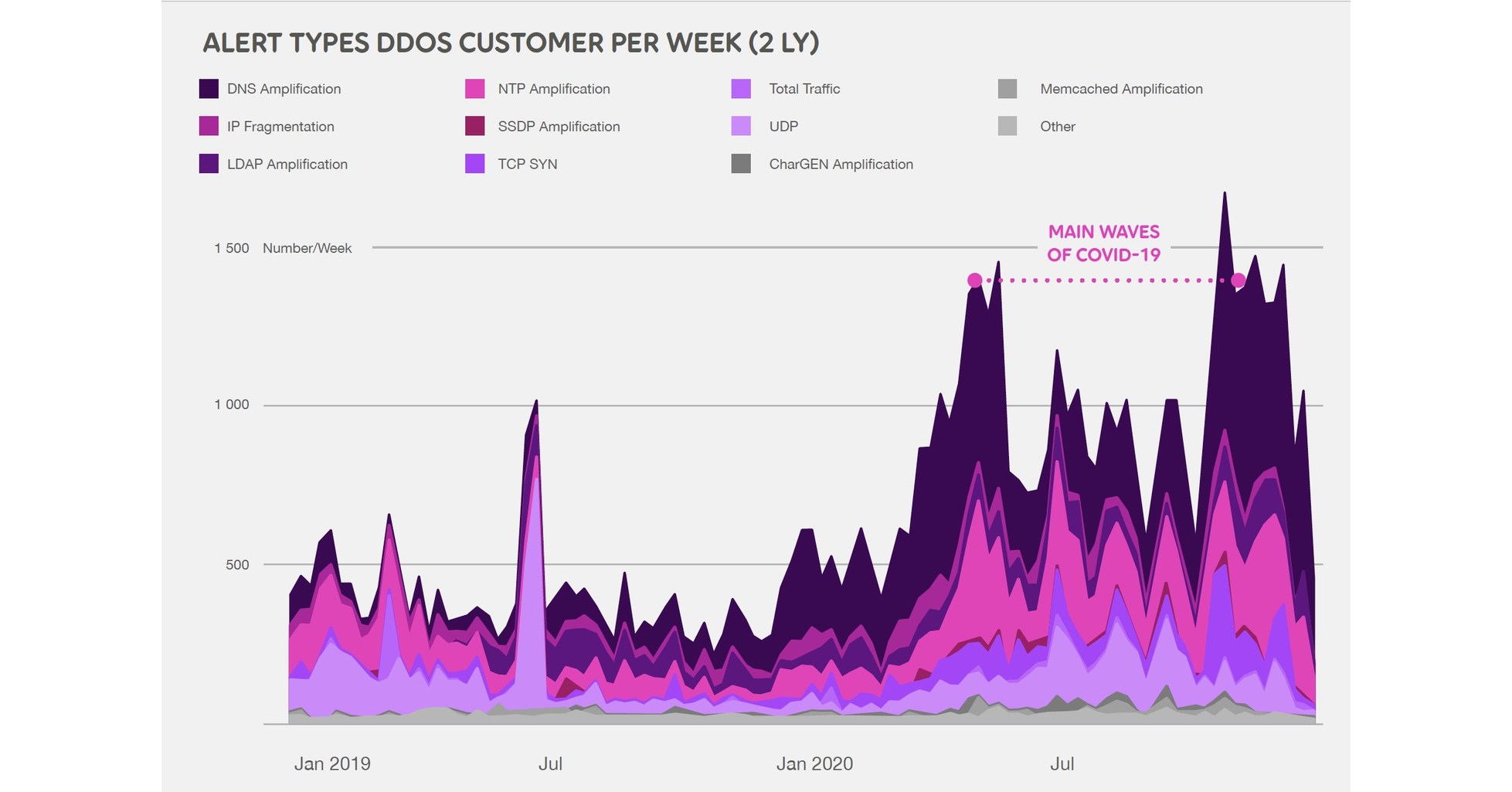
Protocols used for reflection/amplification. Source Arbour Networks,... | Download Scientific Diagram